Researchers have discovered a serious weakness in virtually all websites protected by the secure sockets layer protocol that allows attackers to silently decrypt data that's passing between a webserver and an end-user browser.
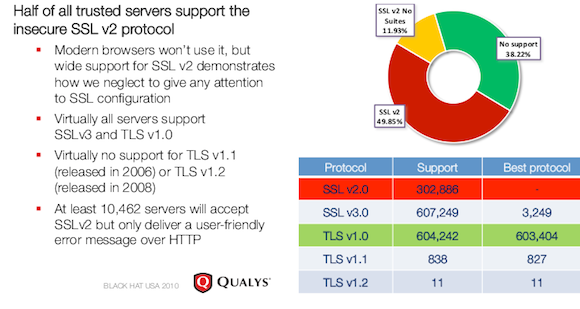
The vulnerability resides in versions 1.0 and earlier of TLS, or transport layer security, the successor to the secure sockets layer technology that serves as the internet's foundation of trust. Although versions 1.1 and 1.2 of TLS aren't susceptible, they remain almost entirely unsupported in browsers and websites alike, making encrypted transactions on PayPal, GMail, and just about every other website vulnerable to eavesdropping by hackers who are able to control the connection between the end user and the website he's visiting.
At the Ekoparty security conference in Buenos Aires later this week, researchers Thai Duong and Juliano Rizzo plan to demonstrate proof-of-concept code called BEAST, which is short for Browser Exploit Against SSL/TLS. The stealthy piece of JavaScript works with a network sniffer to decrypt encrypted cookies a targeted website uses to grant access to restricted user accounts. The exploit works even against sites that use HSTS, or HTTP Strict Transport Security, which prevents certain pages from loading unless they're protected by SSL.
![]()
 http://www.theregister.co.uk/2011/09/19/beast_exploits_paypal_ssl/
http://www.theregister.co.uk/2011/09/19/beast_exploits_paypal_ssl/This is huge guys...pretty much affects Millions of sites which use this tech daily..in fact these sites depend on it. Even though versions 1.1 and 1.2 are immune, its going to take a while to upgrade all the ones running the old versions to the new ones.
It just goes on to show that digital security , even though theoretically safe (in certain instances) is not without loopholes when implemented.